Introduction
Just another writeup for another boot2root Vulnhub Challenge. This one is great to test out different types of exploitation techniques.
Recon
Figure out IP. Ofcourse, when you boot the machine it shows you the IP before the login as well.
LLMNR? Http with admin page?
For LLMNR, I run the following in the hopes of intercepting something at the very least (but to no success)
Exploitation
Trying the usual, I went to the About page to run CeWL on it and get myself a bruteforce dictionary. While doing this, I observed the URL to be interesting.
Hmmm, possible LFI? Let me try.
BAM!!!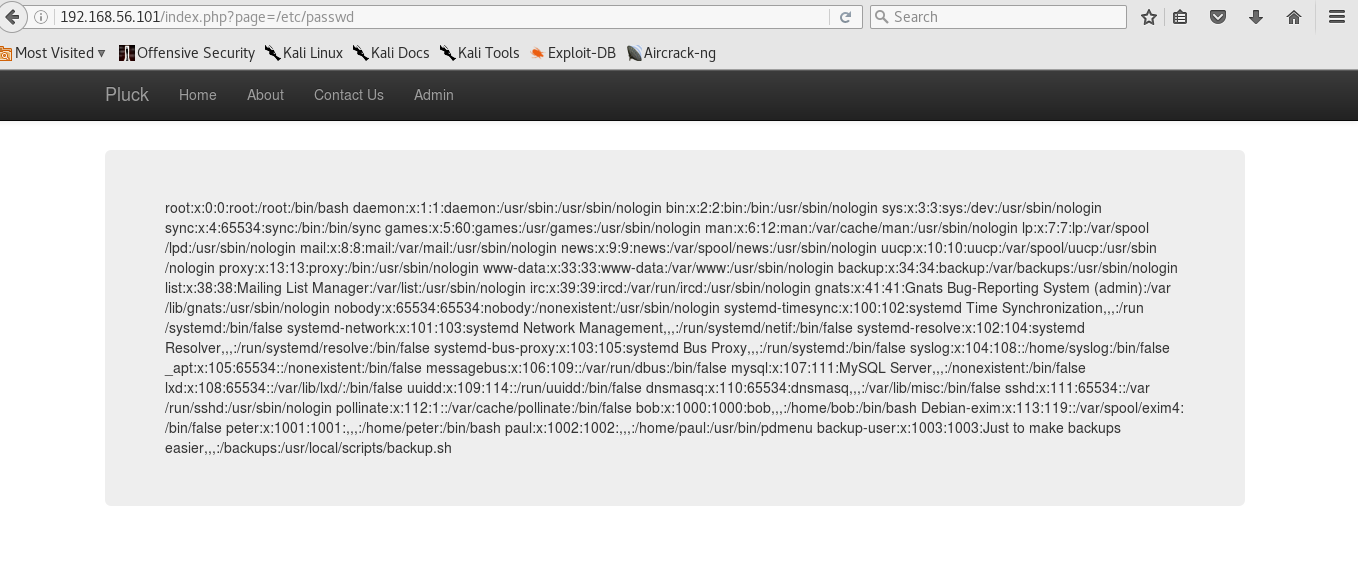
Ok, what did I see here?
|
|
let us call the backup script and see what is being done with this
ahaa! A tar file with all contents for /home and /var/www/html. Let us get hold of it.
At this stage my machines gets stuck (Yes, I am a damn poor boy!). However, after leaving my machine up for a while and having some snacks and returning, it seemed curl had done its best. Next was to untar the file and extract the contents.
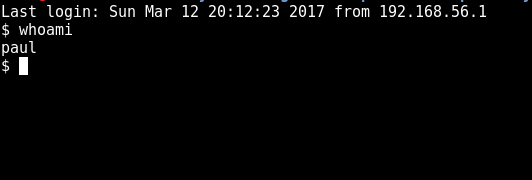
I see the interesting /home/ folder. While searching around, I end up with /home/paul/keys/id_key*. On trying each one of them, I could finally figure out which one was the correct key and was able to ssh into the machine.
And now we have a PDMenu to crack.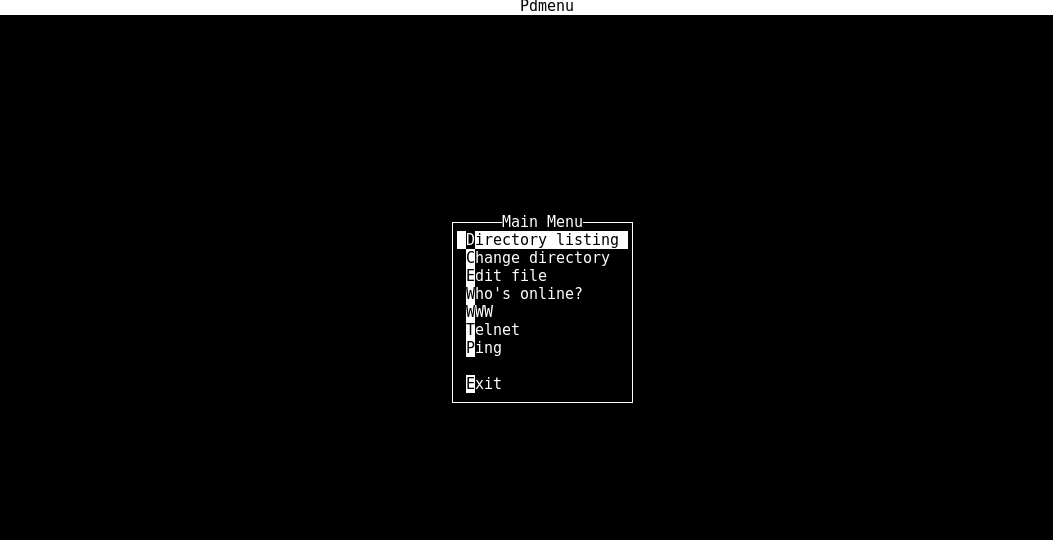
I must say, it took me some time to figure out this one because our dear game writer had set up a lot of honey traps to get you distracted.
Interactive Shell
So, I read an interesting article here. Attempting the same,
|
|
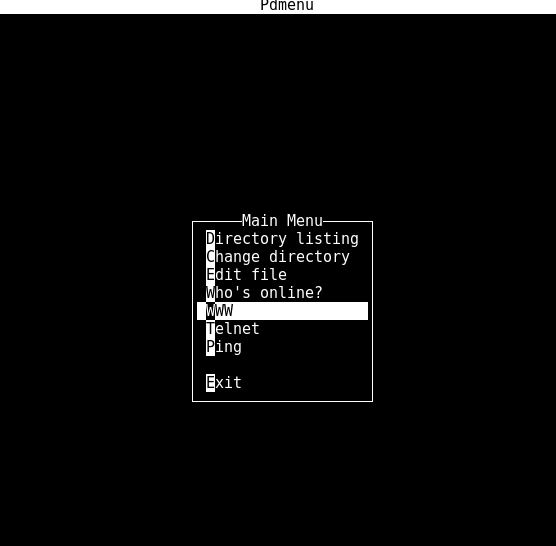
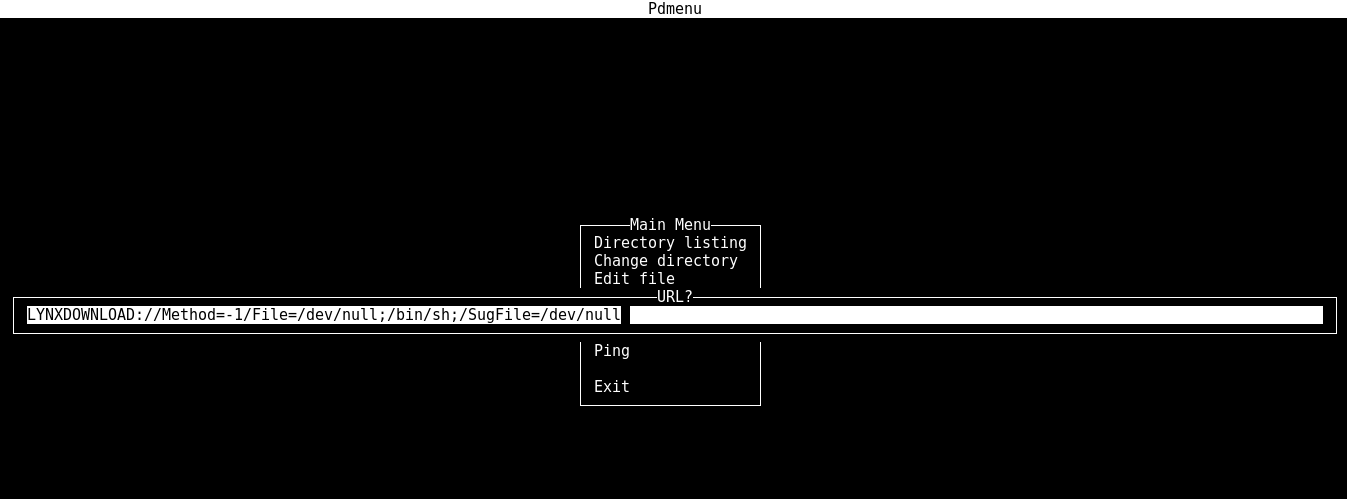
Rooting
The amazing part of this image is there are more than one possible ways of getting an interactive shell. Eventhough I pwn’d this via lynx exploit, while trying to root the system, I figured out there are quite a few ways that we could get access to an interactive shell.
Looking up the systen information and kernel version and other information, there was again more than one possible ways to root this box. Unfortunately on my first attempt (most of them were compilation fails maybe because I didn’t try to rectify the underlying code), keyctl, dirtycow and pkexec race condition (and a few more that failed), this is the enumeration that led to me rooting the box.
|
|
PWNED!
cat /root/flag.txt
|
|