Introduction
Generally ISPs have been very ignorant towards their security, resulting in requirement of the government to enforce policies that would be required ISPs and Telecom Operators to provide the end users a secure and a private communication network. However, due to issues with money, ISPs prefer to relax on most of the security issues or end up hiring firms with external consultants with no idea on how to secure a Telecom Infrastructure. This is the exact reason people would require to audit their own ISPs and make a note of the vulnerabilities. The specific configurational vulnerabilities that would be mentioned in this blog results in not only of an attacker to gain credentials to access internet, but he is also capable of doing crazy number of things while sitting on the same network. The network of this ISP has been the same for more than 2 years now.
Special Mentions
Thanks to Vijay Kumar and Rajesh Deo, Latish Danawale and Shreya. Special thanks to Rushit.
Disclaimer

I, Tanoy Bose, am not responsible for any action that any person with direct or indirect knowledge from this blog, decides to take. I do not encourage malicious behavior and I am a subscribed user of the ISP who is legitimately paying for the subscription and not stealing bandwidth.
My ISP’s setup
A very small diagrammatical representation of my ISP providing internet would be as follows
|
|
Here, a user connects to his WiFi/ ADSL Modem which contains the pppoe credentials that authenticates it with the ISP. Further, the RJ45 network cable coming into my flat gets connected to a switch placed in my apartment. This switch facilitates multiple flats to get access to the ISP. The Access Concentrator is a device that is placed in the ISP’s end that takes care of users to get authenticated with the ISP. Once authenticated, the network is allowed to access the internet.
Hence, I connected my laptop in place of the ADSL WiFi Router-Modem so that I would be in the same broadcast domain of every modem connected to that switch in my apartment. Evil Thoughts
Reconnaisance
The scene was set in my new flat with nothing available, other than a network cable. The hack initially began with my tingling hacker-sense to attempt and fiddle with this available RJ45 port.
1. Plug in the RJ45 cable
Not much to stay for this. However, we were lucky that when we plugged in the ethernet chord, we received an IP address.
|
|
2. Turn on the wireshark
But obvious! When you hit any unknown network, check out the super awesome network sniffer - Wireshark!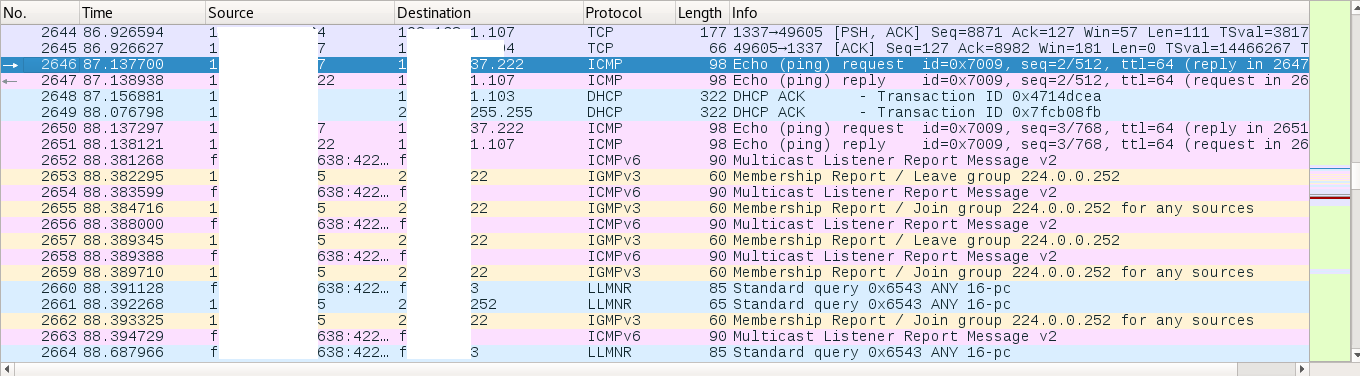
3. Probing around
Figuring out the network is always requires a huge time to invest. Often, significantly larger than the exploitation phase. But understanding the functionality of a black box can only be done only if we extensively probe it. Hence we begin!
Netdiscover
The ARP requests, the best way to find out your neighbouring systems along with their MAC addresses. There are two ways to run this. One is the passive mode
|
|
The other is the more active arp of a specific range. My choice of range would be my current broadcast range.
|
|
Responder
Another beautiful tool to detect vulnerable broadcast packets like LLMNR and NBNS present in the network.
|
|
Bettercap
Just like responder, bettercap spoofs NBNS requests and is able to do man-in-the-middle attack in the LAN.
To run better cap in spoofing and discovery mode, just run it.
|
|
To run better cap in spoofing, discovery, sniffer, intercepting http and https requests, targetting specific IP only -
|
|
NMap
And ofcourse, what is reconnaisance without the hacker’s favourite network mapper? We do a simple nmap Ping Scan on the network ranges of our choice. My first scan range is going to be our current broadcast range.
|
|
At this point, it was clear I was connected to an isolated network segment without access to internet. Damn! So I go through the entire wireshark logs again.
After going through the logs over and over trying to identify vulnerable protocols, luck struck and the electricity in my apartment tripped. This resulted in all the routers to disconnect. The second the electricity returned, I was flooded with a certain type of packet - PADI.
Authentication Technology
Upon reading through a couple of RFC(s) (2516, 4938, 5578), I could understand the 5 critical PPPoE packets. Infact, it is not very different from the concept of 3 way handshake, except that this has session management involved in it.
PADI (PPPoE Active Discovery Initiation) - Broadcast packet - Sent from Client to the broadcast network - According to RFC, needs to contain Source MAC and a Service Name Tag.
(talk about access concentrator)
|
|
PADO (PPPoE Active Discovery Offer) - Access Concentrator to Client - Offer, along with it’s AC Name that and can do the work for the Service Name Tag of PADI.
|
|
PADR (PPPoE Active Discovery Request) - Client to Access Contentrator - To establish session with the Access Concentrator
|
|
PADS (PPPoE Active Discovery Session) - Access Concentrator to Client - Accept the PADR and start with Authentication. Authentication types can be PAP, CHAP, MS CHAP, etc.
|
|
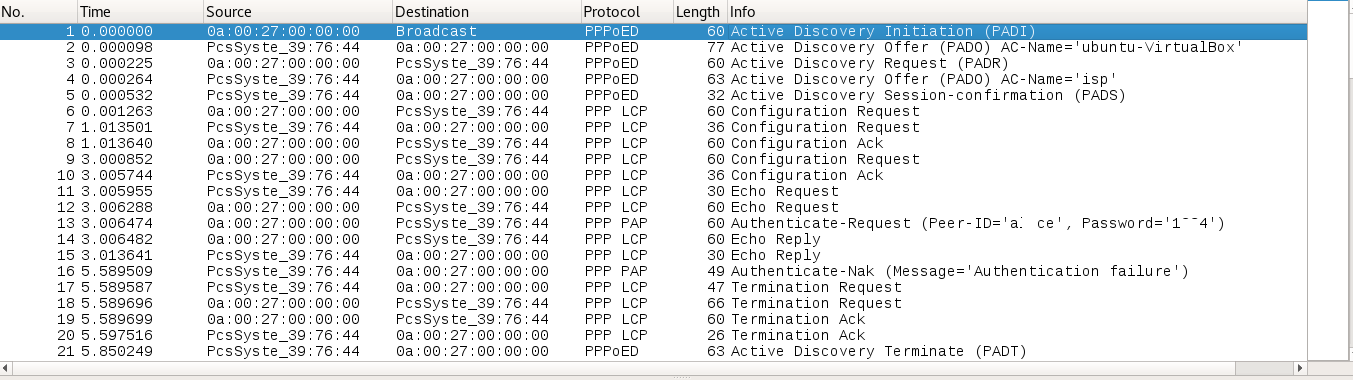
Though it would make sense to mention PAP (Password Authentication Protocol) over here. At a later stage, you will understand why I did this. PAP is quite simple. The packet is called PPP LCP (Point to Point Protocol Link Control Protocol) and the process is as follows -
|
|
PADT (PPPoE Active Discovery Terminate) - Client to Access Concentrator - The giant logout button :D
|
|
Here is a screenshot of the capture of PPPoE-PAP authentication process.
Technical setup
A very quick run through on what we need
Prior to going into the Hacking, would recommend everyone to prepare with the setup. For this hack, we are going to need the following
Ubuntu installed on Virtual Box with PPPoE server
PPPoE Driver
Confifguring PPPoE/ ADSL Connections - PPPoEConf
To send PADT requests - pppoesk
1. Ubuntu on Virtual Box with PPPoE Server
|
|
Configurational changes are required to be made in this server
|
|
To route traffice from one interface to another, you can do as follows. This is something that you a hacker might do when he would want to route all the traffice from his system to a different interface giving connection to the internet. I do not recommend anyone from attempting this. Here, you authenticate yourself from the eth0 port and have the pppoe server listening on eth1 port. All traffic recieved on eth1 can be redirected to eth0. However, I utilize the pap-secrets as a database to store all the credentials I harvested. That way, I replicate the ISP’s behaviour completely and do not give unauthenticated internet access. I can also target specific users/ flats in my apartment by allowing on those IDs to connect to the internet and intercepting their traffic.
|
|
2. PPPoE Driver
|
|
3. Configuring PPPoE/ ADSL Connection - PPPoEConf
|
|
4. To send PADT requests - pppoesk
|
|
Technical pew-pew-pew
Stage 1 - PADI
The wonderful part is, this is a broadcast request - PADI. Anyone in the network can broadcast connection request to me. Awesome!
|
|
Now since I am the immediate next hop of this system (and I am way closer to the apartment switch as compared the access concentrator), I am confident of the fact that my response to the client system would be way faster than that of the valid AC’s response.
However, to receive this PADI request, there must be new connection attempts being made. Electricity! I turned off the mains of my apartments for a couple of seconds, and as soon as I had them back on, I could see approximately 6 PADI requests.
Stage 2 - Hosting a fake Access Concentrator
To mimic the behaviour of the Access Concentrator, we launch the pppd that we had setup in our Virtual Machine and capture all network traffic coming to it.
A step by step guide to setting up your own PPPoE server and configuring it is available at this site, else you could follow the setup guide.
For capturing the password, we don’t really need any other setup/ customization for capturing the passwords of the users attempting to connect. However, we do need the users to attempt to connect. But for this to happen, I needed to take risk of going and getting caught while playing around with the mains. Hence now I used the trick of the Giant Logout Button - The PADT request.
Stage 3 - Disconnecting users with PADT
Here I assume you already have got pppoesk installed following the setup guide above. As an alternate to pppoesk, we could also use pppoe-killer.
Ok, so we have the PADI requests in which we have the MAC address of all our neighbours. We now keep pppoesk running and connect to the port.
|
|
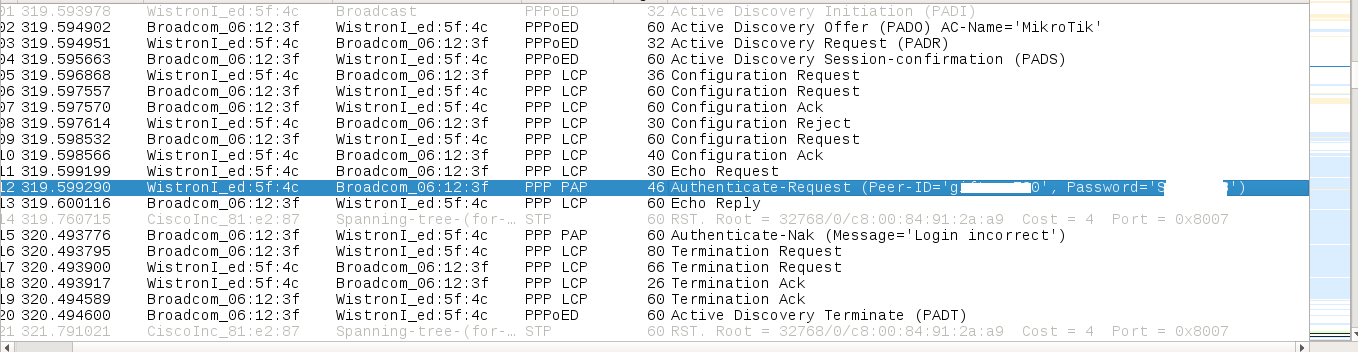
As soon as we get a PADI request from the Access Concentrator, we send it a PADT with a spoofed MAC and deauthenticate the original router. Once this happens, we make alive our honey-trap pppoe server and wait for the victim’s router to auto-reconnect. The second the router attempts to reconnect, it connects to the honeytrap server and loses it’s credentials.
These credentials can be used to authenticate your own system on the ISP and gain access to internet. :)
FUN FACT: Most ISPs don’t enforce CHAP/ MSCHAP authentication, hence routers are configured to use any type of authentication. This means, even if the ISP is capable of using it, we can downgrade the authentication mechanism to PAP and get the credentials in plain text. Below is the capture of my own, valid ISP credentials. :)
Perks of the Hack
If you are one of those who jumped to the bottom of this blog because of “tl;dr” feeling, here is why you should read the entire blog.
1. Free Internet
Of course, by the end of capturing one credential, we could use this credential, configure it on our pppoeconf and send it to the Access Concentrator for PROFIT! But would a malicious user actually stop here?
2. Big Brother is your neighbour
A malicious user would anyday prefer going one step ahead and poison the entire traffic in the network.
This blog post beautifully explains on how to setup a real PPPoE server.
So here is what you can do,
|
|
Personally I utilize bettercap and have much fun and such pwn with it to perform man-in-the-middle attacks.
What can the ISPs do?
Enforce stronger authentication mechanisms like PPPoE-CHAP, with a strong password policy for the same.
Have good session management by not allowing more than one session for any userid at the same time.
For any further queries/ help fixing your network, you can contact me. Do remember, I do not look for money rather I care more about respect. :)
What should an end user do?
You are not safe. Utilize VPN/ VPS. Careful when you use websites without SSL. Extra careful if all your certificates have suddenly changed and begin warning you. Do not trust your ISP. Audit the security of your ISP yourself.
Take care. You are not alone. :)